Packet Sniffing with Wireshark
Objective:
Download and install Wireshark, use as a packet sniffing protocol analyzer.
Equipment List:
– Computer
– Windows
– Wireshark
Notes and Observations:
We began by downloading and installing the latest version of Wireshark. Then we began to capture packets during the following activities:
- Browse to a webpage on a server outside of campus.
- Do a file transfer to an FTP server.
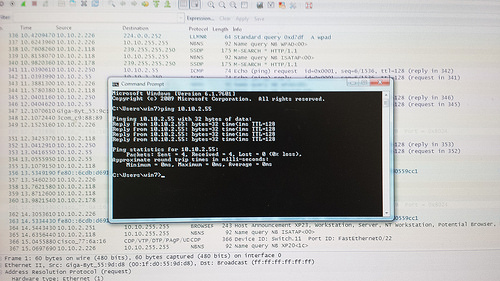
- Test connectivity to a host with Ping.
- Acquire a network address with DHCP.
- One other experiment of your choosing. (ping another computer on our network)
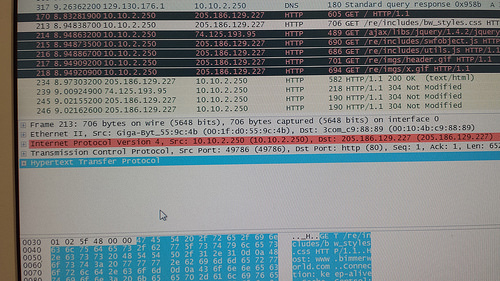
After that, we selected various packets in the top pane to find the frame’s protocol type, length, source & destination address information. While gathering information, we compared the similarities and differences. After finding frames containing DNS, ICMP, HTTP, ARP, and HTTP GET information, we analyzed the process of DHCP configuring IP addresses.
Diagrams, Flowcharts, and Figures:
References:
Questions:
1.) Find the frame’s protocol type, length, source & destination address information. Locate sequence numbers used by a TCP segment. What is the purpose of these numbers? View other protocol header information. List the field values of one of the protocol headers such as IP, TCP, or UDP.
– IP, 60 bytes
– ff:ff:ff:ff:ff:ff
– 00:1f:d0:55:90:d8
2.) Find the FTP protocol frames that show where your username and password were supplied. What do you notice about these frames? What can you say about the security of the FTP protocol after viewing these frames? Can you locate frames that use the “GET” and “PUT” commands used to download & upload files? Describe what you have learned about the process of an FTP transfer by viewing these packets.
– Shows “pass” and “user”
– Not secure
– Everything is listed in order of procedure
3.) Find a frame containing a DNS query. What protocols are encapsulated in this frame? Which of these protocols is a transport layer protocol?
– IP, UDP
– UDP
4.) Find a frame containing ICMP information. What protocols are encapsulated in this frame? Which layer does ICMP reside in? What do the ICMP initials mean?
– IPv6
– Layer 3/4
– Internet Control Message Protocol
5.) Find frames containing HTTP information. Approximately how many frames did it take to download the web page? List the different protocols that are used. Note how many protocols are working together to find and retrieve the information.
– 678 bytes
– Ethernet, IP, TCP, HTTP
6.) Open the first HTTP Response frame. Find the type of web server being accessed in this frame’s header.
– Ethernet II
7.) What is the process for a machine to be assigned an IP address using DHCP?
– When a computer or other networked device connects to a network, its DHCP client software in the operating system sends a broadcast query requesting necessary information. Any DHCP server on the network may service the request. The DHCP server manages a pool of IP addresses and information about client configuration parameters such as default gateway, domain name, the nae servers, time servers.
8.) What is the purpose of sequence numbers?
– Help TCP reorder packets that are sent
9.) What is the purpose of source & destination addresses?
– To figure out where data came from, and where it needs to go
10.) What is the purpose of DNS?
– Translates internet addresses into IP addresses
11.) What is DHCP?
– Domain Host Configuration Protocol
12.) What is the relationship between the OSI model of networking and the TCP/IP model you saw in this lab activity?
– Both layered models, used to represent a computer network (physical/software).
13.) What evidence of layered network design did you discover when examining the captured data? How does the wireshark data demonstrate encapsulation?
– Structured protocol with procedure
– Encapsulation was shown in many frames and packets
14.) What are the implications of having a tool like Wireshark freely available? For network administration? For security?
– For both, but could easily be used for illegal sniffing and “tapping”
Conclusions:
Very interesting to see exactly what was going on with various protocols. They are many steps and “hoops” to jump through just to load a single web page, at least seemingly to the human eye.